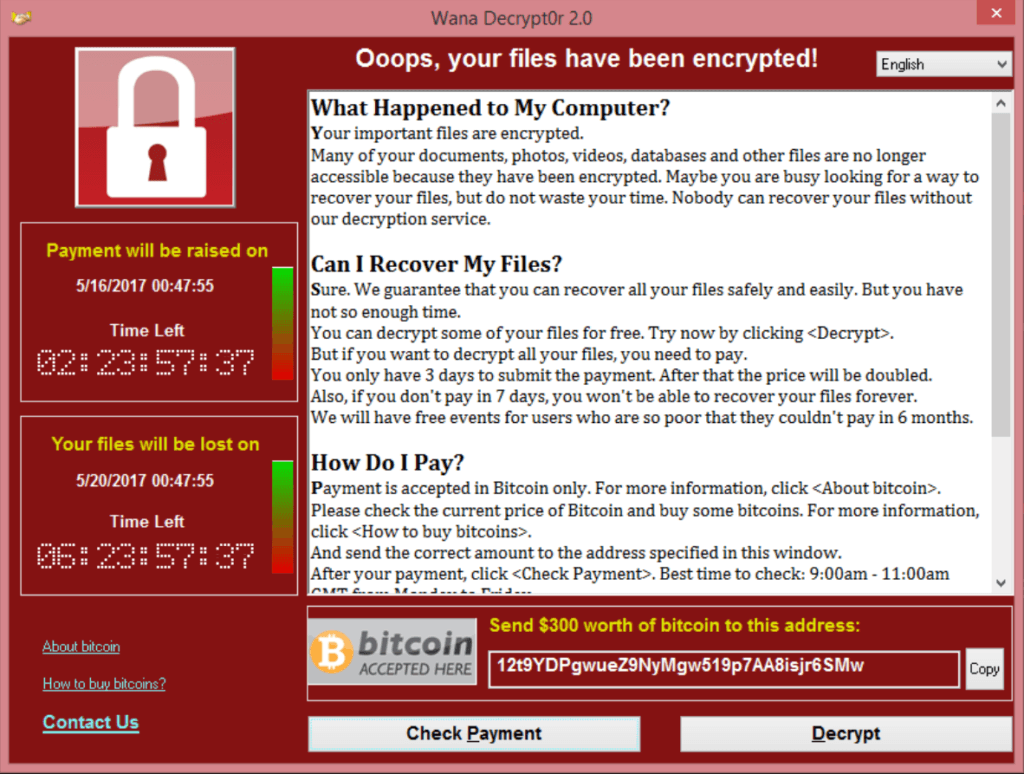
Ransomware is a form of malicious software program, a virus. In particular, a virus which removes access to data and only restores access to that data once a ransom has been paid to the creators.
Ransomware uses a mathematical computing technique called encryption. Encryption works a bit like a lock and key. The lock is a mathematical formula which turns your important documents, photos, media and any other data into an unrecognisable stream of digital data. The mathematical formula can only be reversed using the correct corresponding ‘key’, something which the Ransomware creators have, but you don’t. Without this key, your data can never be converted back into it’s original form and therefore will remain lost forever. The ransomware attack usually pops up a notice instructing the user to take certain actions to make a payment of a substantial amount of money before the key is released and the data is obtainable again. To make matters worse, the attack usually gives you a very limited window to make your payment, after which the data is lost forever.
The NHS (like many organisations) has some difficult challenges which are met by creating bespoke software systems. The NHS in particular has to deal with a huge amount of data relating to patients, staff, medication, purchasing etc, many of these systems are created specifically for the task, and many of them were made a long time ago. Many government systems still rely on software that was written in the 70’s and 80’s. This is because those systems still work and are so largely integrated into the daily operation that to replace or remove them would be incredibly expensive.
In the case of the NHS, some of these software solutions were reliant on Windows XP to operate. However, Microsoft stopped supporting Windows XP in 2014. This means that any security vulnerabilities identified after this time would not be addressed, and this is the method of action used by the attackers of the NHS. The use of Windows XP was widespread, and it’s security features were flawed. The NHS was running the risk that it’s system could be infected, but no doubt the cost of upgrading these systems to a newer and safer Windows environment would have cost millions of pounds.